1. Create a Domain User Account (e.g. MSCRM4Service) using the dsa.msc tool (Active Directory Users and Computers).
2. On the MSCRM Web Server, launch the Internet Information Services (IIS) Manager, locate the CRMAppPool and right click Properties. Go to the Identity Tab, and change the Application Pool Identity to the Domain User Account.

3. Add the Domain User Account to the local group (on the MSCRM Web Server): CRM_WPG (CRM Worker Process Group).

4. Add the Domain User Account to the local group (on the MSCRM Web Server): IIS_WPG (IIS Worker Process Group).

5. Add the Domain User Account as a member to the SQLAccessGroup in the Active Directory (please take note of the proper GUID for the SQLAccessGroup).

6. Add the Domain User Account as a member to the PrivUserGroup in the Active Directory (please take note of the proper GUID for the PrivUserGroup).

7. Create a Login for the Domain User Account in the SQL Server.
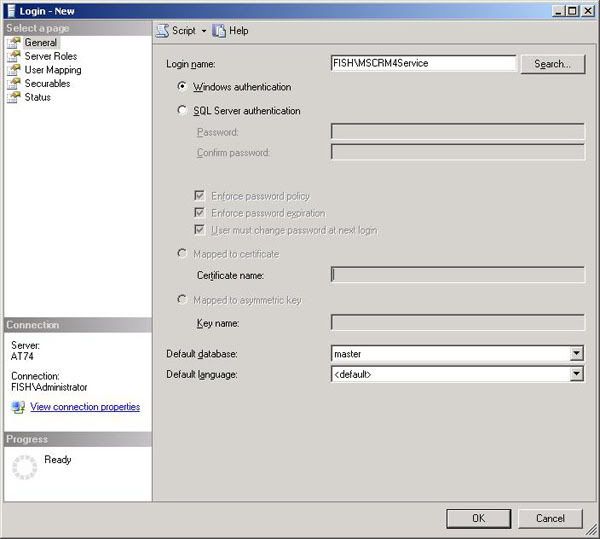
8. Configure appropriate mappings for the Domain User Account for databases MSCRM_Config and Organization_MSCRM, assign the db_owner role for both.

9. Launch ADSI Edit (adsiedit.msc)
10. Expand node Domain [Domain Name]
11. Expand node start with DC= under the domain node
12. Expand node CN=Users
13. Locate the Domain User Account created in Step 1 (e.g. CN=MSCRM4Service), right click and select Properties

14. Locate the Attribute servicePrincipalName and click on Edit. Add following entries:
• HOST/HostName
• HOST/HostName.FQDN (Fully Qualified Domain Name)

15. Restart the MSCRM Server.